Cyber Incident Reporting for Critical Infrastructure Act of 2022
What you need to know and how to prepare for the requirements.
Table of contents
On March 15, 2022, the Cyber Incident Reporting for Critical Infrastructure Act of 2022 was signed into law by President Biden as part of the Consolidated Appropriations Act of 2022. The act will require US-based privately-owned businesses, operating in critical infrastructure sectors, to report cyber security incidents and ransomware payments to the United States federal government. However, there are still guidelines yet to be established by the federal government as far as the implementation of the law. As Information Technology Professionals, you should be familiar with these new requirements and how to prepare your organization when the law is finally implemented.
In this blog, I will attempt to break down this federal act as best as possible to give you an insight into what may or may not be required by federal law for your organization The views and opinions expressed in this blog post are of my own professional opinion and not of my employer or organizations with which I am affiliated. I will be referencing analyses from other individuals and organizations which may provide further information on the passed legislation. Readers of this blog should contact their organization’s attorney to obtain appropriate legal advice.
I am not a lawyer, and this is not legal advice.
What is CIRCIA?
In general, the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) amends Title XXII of the Homeland Security Act of 2002 and requires covered private-sector entities to submit reports to the Cybersecurity and Infrastructure Security Agency (CISA) when they suffer a “covered cybersecurity incident or make a ransomware payment” within 72 hours after the incident has occurred. (H.R. 2471 § 2242(a)(1), H.R. 2471 § 2242(a)(2))
A covered private-sector entity would also be required to submit a supplemental report to CISA if “substantial new or different information becomes available or if the covered entity notifies the Agency (CISA) that the covered cyber incident at issue has concluded and has been fully mitigated and resolved. (H.R. 2471 § 2242(a)(3))
A covered private-sector entity, subject to the requirements, would also be required to preserve data relevant to the covered cyber incident or ransom payment in accordance with the procedures established in the final guidelines issued by CISA. (H.R. 2471 § 2242(a)(4))
There are some exceptions to the requirements (H.R. 2471 § 2242(a)(5)), Section 2242 outlines the required reporting of covered cyber incidents, ransomware payments, supplemental information, the preservation of information, and any exceptions.
What is a Covered Private-Sector Entity?
Section 2240 (Definitions) of Title XXII of the Homeland Security Act of 2002 defines a covered entity as, “an entity in a critical infrastructure sector, as defined in Presidential Policy Directive 21, that satisfies the definition established by the Director (of the Cybersecurity and Infrastructure Security Agency) in the final rule issued pursuant to section 2242(b).”
Presidential Policy Directive 21 (PPD-21) identified the following 16 critical infrastructure sectors:
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Healthcare and Public Health
- Information Technology
- Nuclear Reactors, Materials, and Waste
- Transportation Systems
- Water and Wastewater Systems
The reference to “...the definition established by the Director in the final rule issued pursuant to section 2242(b).” would come from the final ruling and from CISA on which private-sector entities would also be required to report.
If your organization falls within any of the critical infrastructure sectors, as defined in PPD-21, or designated by CISA after final rules have been published, you will potentially be required to report these incidents. It may be some time before CISA publishes these final guidelines, and CISA will be required to conduct an outreach and education campaign to let covered entities know about the reporting requirements (H.R. 2471 § 2242(e) - Outreach to Covered Entities).
What is a Covered Cybersecurity Incident?
Section 2240 defines a covered cyber incident as a “substantial cyber incident experienced by a covered entity that satisfies the definition and criteria established by the Director in the final rule issued pursuant to section 2242(b).” This essentially means whatever criteria CISA defines as a substantial cyber incident when final guidelines are published.
Section 2242(c)(2)(A) does state, at a minimum, what would constitute a covered cyber incident. This includes the following:
- A cyber incident that leads to substantial loss of confidentiality, integrity, or availability of such information system or network, or a serious impact on the safety and resiliency of operational systems and processes;
- A disruption of business or industrial operations, including due to a denial of service attack, ransomware attack, or exploitation of a zero-day vulnerability, against an information system or network, or an operational technology system or process;
- Unauthorized access or disruption of business or industrial operations due to loss of service facilitated through, or caused by, a compromise of a cloud service provider, managed service provider, or other third-party data hosting provider or by a supply chain compromise
Again, CISA will produce final guidelines on what is considered to be a covered cyber incident and what will need to be reported.
How does CIRCIA define Ransom Payment and Ransomware Attack?
Section 2240 defines ransom payment as “the transmission of any money or other property or asset, including virtual currency, or any portion thereof, which has at any time been delivered as ransom in connection with a ransomware attack.”
Section 2240 also defines ransomware attack as “an incident that includes the use or threat of use of unauthorized or malicious code on an information system, or the use or threat of use of another digital mechanism such as a denial of service attack, to interrupt or disrupt the operations of an information system or compromise the confidentiality, availability, or integrity of electronic data stored on, processed by, or transiting an information system to extort a demand for a ransom payment.”
This does not include any event where the demand for payment is “not genuine” or is “made in good faith by an entity in response to a specific request by the owner or operator of the information system”.
Overall, if a malicious actor has infected your organization’s systems through the use of a ransomware attack and has demanded a ransom payment, you will be required to report the incident to CISA.
What Information Would you Need to Report?
As we wait for clarification and guidelines from CISA, Section 2242(c)(4) does provide us with an outline of what information will need to be given when reporting a covered cyber incident. This information will include a description of the covered cyber incident that includes:
- Identification and a description of the function of the affected information systems, networks, or devices that were, or are reasonably believed to have been, affected by such cyber incident;
- A description of the unauthorized access with substantial loss of confidentiality, integrity, or availability of the affected information system or network or disruption of business or industrial operations;
- The estimated date range of such incident; and
- The impact on the operations of the covered entity (your organization).
Other details of reporting would include the following (where applicable):
- A description of the vulnerabilities exploited and the security defenses that were in place, as well as the tactics, techniques, and procedures used to perpetrate the covered cyber incident.
- Any identifying or contact information related to each actor reasonably believed to be responsible for such cyber incident. -Identification of the category or categories of information that was, or are reasonably believed to have been, accessed or acquired by an unauthorized person.
Section 2242(c)(5) outlines what information will need to be given when reporting a ransomware payment. This will include the following if applicable and available:
- A description of the ransomware attack, including the estimated date range of the attack.
- A description of the vulnerabilities, tactics, techniques, and procedures used to perpetrate the ransomware attack.
- Any identifying or contact information related to the actor or actors reasonably believed to be responsible for the ransomware attack.
- The name and other information that clearly identifies the covered entity that made the ransom payment or on whose behalf the payment was made.
- Contact information, such as telephone number or electronic mail address, that the CISA may use to contact the covered entity that made the ransom payment or an authorized agent of such covered entity, or, where applicable, the service provider of such covered entity acting with the express permission of, and at the direction of, that covered entity to assist with compliance with the requirements.
- The date of the ransom payment.
- The ransom payment demand, including the type of virtual currency or other commodity requested. -The ransom payment instructions, including information regarding where to send the payment, such as the virtual currency address or physical address the funds were requested to be sent to.
- The amount of the ransom payment.
Again, CISA will be providing final guidelines and educational material to help your organization meet the requirements of reporting. You will likely see these questions already provided to you in an online form during reporting.
What could happen if your organization does not report?
Section 2244 outlines noncompliance with required reporting. If your organization fails to comply, the CISA may issue a subpoena in a district court of the United States “to gather information sufficient to determine whether a covered cyber incident or ransom payment has occurred.” Section 2242(c)(2)(C) states, “A court may punish a failure to comply with a subpoena issued under this subsection as contempt of court.”
What should your organization do?
Even though this law is not in full effect, it is strongly recommended that you should already be reporting critical cybersecurity incidents or ransomware attacks to law enforcement or to a government organization that can properly assist you in dealing with these matters.
In the United States, these organizations include the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation’s (FBI) Internet Crime Complaint Center (IC3). You can also contact your local U.S. Secret Service Cyber Fraud Task Force Network Intrusion Team. These organizations will be able to initiate criminal investigations and offer their assistance to the best of their abilities.
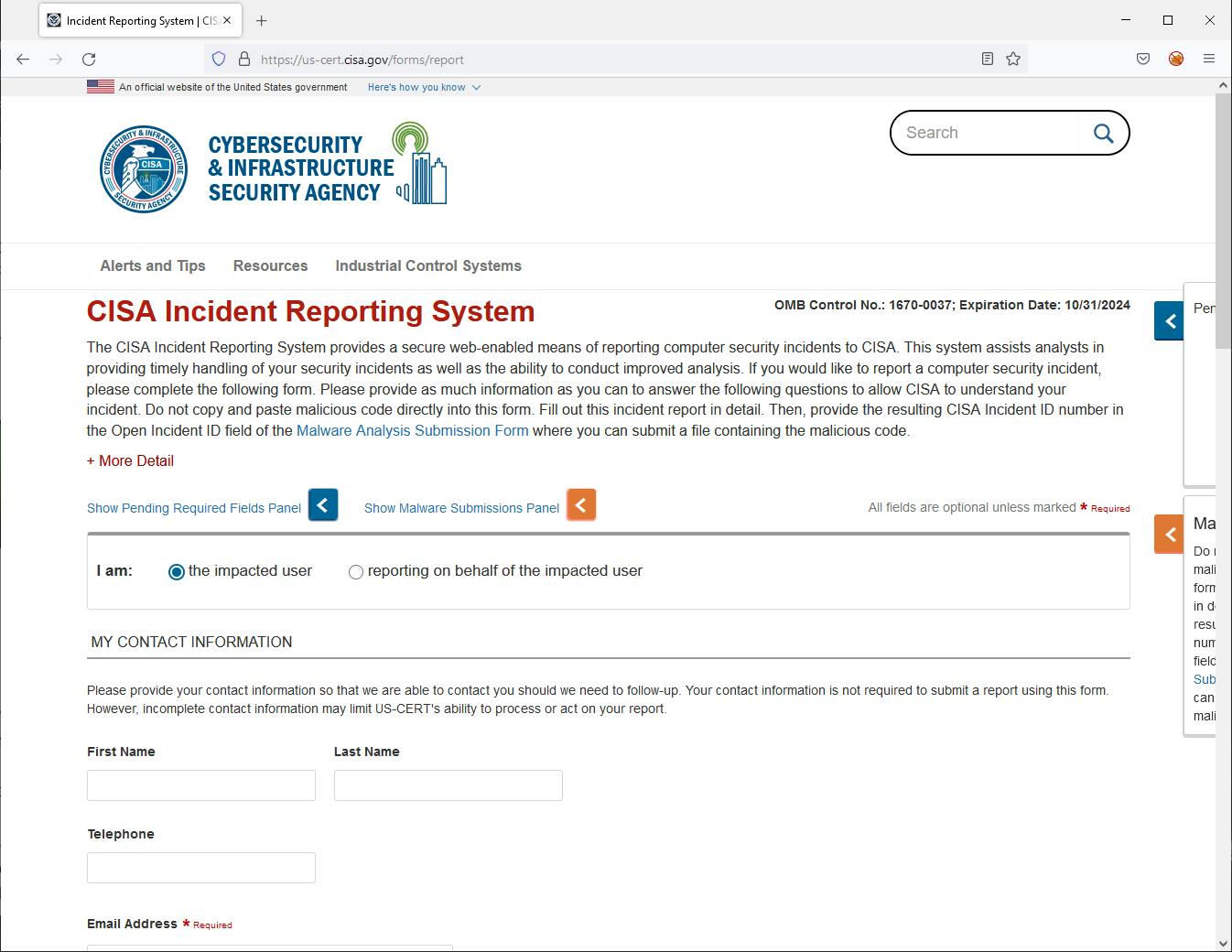
As an organization, you should also look to implement technologies and procedures to help prepare for the upcoming requirements.
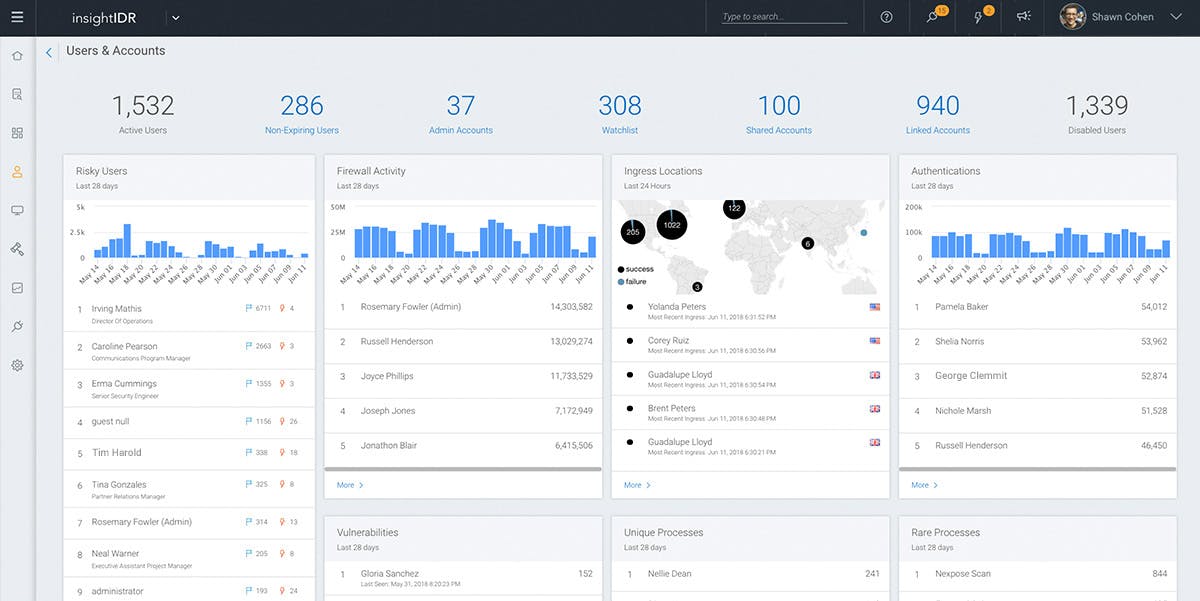
One good technology system to implement would be a SIEM (pronounced "sim"). A Security Information Event Management (SIEM) is a system designed to college system log (Syslog) messages from all your security appliances, networking devices, servers, and workstations into a single unified environment. A SIEM can offer real-time monitoring and analysis of events as well as tracking and logging of security data for compliance or auditing purposes. (ref. What is SIEM? - IBM)
There are various providers of SIEM applications that are out there on the market such as:
- Splunk Enterprise SIEM
- IBM QRadar
- SolarWinds SIEM Security and Monitoring
- Datadog
- AlienVault USM
- Rapid7 Insight IDR
There are also Free and Open-Source SIEM tools which are usually limited in their capabilities compared to their paid/enterprise versions.. This list includes:
- AlienVault OSSIM
- SIEM Monster Community Edition
- Wazuh
- Snort
- OSSEC
- Sagan
- Logit.io
- Prelude
- Splunk Free
- Security Onion
- Suricata
- Greylog
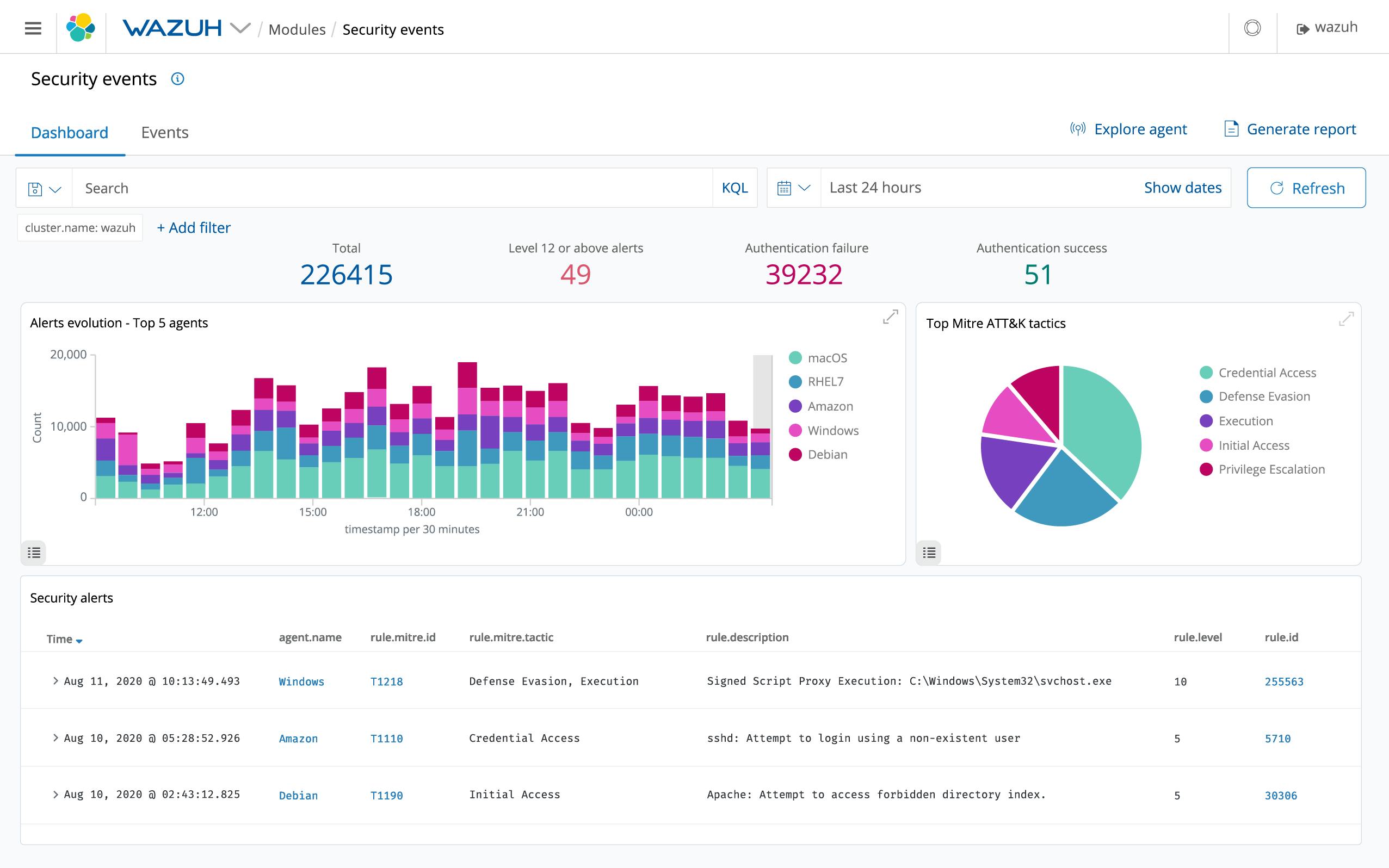
Analysis of the free and open-source products listed above can be found in this blog post of the THE TOP 14 FREE AND OPEN SOURCE SIEM TOOLS FOR 2022.
A good procedure to implement would be an Incident Response Plan. An Incident Response Plan is a set of tools and procedures that your security team can use to identify, eliminate, and recover from cybersecurity threats. It is designed to help your team respond quickly and uniformly against any type of external threat.
Being prepared to respond to an incident and having documented steps on how to respond and recover from an incident can save your organization critical time and money. Part of the Incident Response plan includes properly documenting and reporting the incident.
For more information on building your own Incident Response Plan, please visit the following resources:
Conclusion
The above information was just a high-level overview of the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) and its impending requirements for covered privately-owned companies operating in critical infrastructure sectors. It is likely that CISA will produce final guidelines within the next 18-24 months. However, you should immediately begin preparing your organization to meet these requirements when they are finally implemented.
For further information on this newly signed law, I will include some legal analyses which I found to be helpful.
I thank you for your time in reading this blog post and I hope that you found it informative and helpful. Please feel free to comment below or share with your network. Thank you!
(Blog image photographed by Harold Mendoza on Unsplash)

